 As a Managed Security Service Provider (MSSP) for Department of Defense (DoD) contractors throughout the United States it is one of our missions to keep Defense Industrial Base (DIB) companies updated on DFARS requirements and the rollout of CMMC. This is so they can meet the DoD’s cybersecurity requirements and continue to offer their products and services to the department without any delays or surprises.
As a Managed Security Service Provider (MSSP) for Department of Defense (DoD) contractors throughout the United States it is one of our missions to keep Defense Industrial Base (DIB) companies updated on DFARS requirements and the rollout of CMMC. This is so they can meet the DoD’s cybersecurity requirements and continue to offer their products and services to the department without any delays or surprises.
With that said, it is critical for DIB companies to understand that the Defense Contract Management Agency (DCMA) is currently conducting random DIBCAC assessments on company’s IT systems to enforce DFARS 7019 and 7020. For contractors who have either failed to start implementation of cybersecurity requirements or have put them on hold, we advise to have them completed immediately.
What is the DCMA?
The DCMA provides contract administration services for the Department of Defense (DoD) and is an essential part of the acquisition process. The agency manages 250,000 contracts, valued at more than $3.5 trillion. DCMA makes sure DoD, other federal agencies, and partner nation customers get the equipment they need, delivered on time, at projected cost, and meeting all performance requirements.1
What is DIBCAC?
DCMA oversees the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). DIBCAC is a team of technology professionals that perform two primary missions:
- Assess DIB Supplier Cybersecurity: Assess DIB companies to ensure they are meeting contractually required cybersecurity standards. The team ensures contractors have the ability to protect controlled unclassified information for government contracts they are awarded.
- Establish & Expand CMMC Assessment Capabilities: The DIBCAC is also a member of the government team establishing the Cybersecurity Maturity Model Certification (CMMC) program to expand cyber assessment capabilities throughout the defense industrial base.
Source: https://www.dcma.mil/News/Article-View/Article/2981222/tech-team-wins-cybersecurity-award/
What are DIBCAC Assessments?
DIBCAC assessments are essentially audits of DoD contractor systems to ensure they have implemented the security controls of NIST 800-171 as required by DFARS 7019 & 7020.
According to John Ellis, the Technical Directorate’s Software Division director at DCMA, the following are problems that they are seeing regularly with the audits they have completed so far:
- Lack of Multi Factor Authentication (MFA)
- Poorly written or non-existent policies
- Lack of FIPS 140-2 validation for encryption solutions
- Poorly designed/implemented network segmentation
If a DoD contractor fails to pass a DIBCAC assessment, they may be ineligible to provide their products and services to the DoD. Because these assessments are currently being conducted, it is essential that suppliers are prepared now.
Where to Get Help & How to Prepare
The laws and requirements of DFARS and CMMC can be daunting for many DoD contractors — especially those that lack the resources and knowledge to implement security controls themselves. As a DFARS and CMMC consultant, we help DoD suppliers navigate the complexities of the DoD’s cybersecurity policies and have a team of cybersecurity professionals to implement security controls on their behalf.
To learn more about how to prepare for CMMC, visit our CMMC preparation guide. Also, feel free to give us a call or request on consultation. Whether you’re a small or large company, we’re happy to discuss your unique situation and help you find the best path to preparing for a DIBCAC assessment.
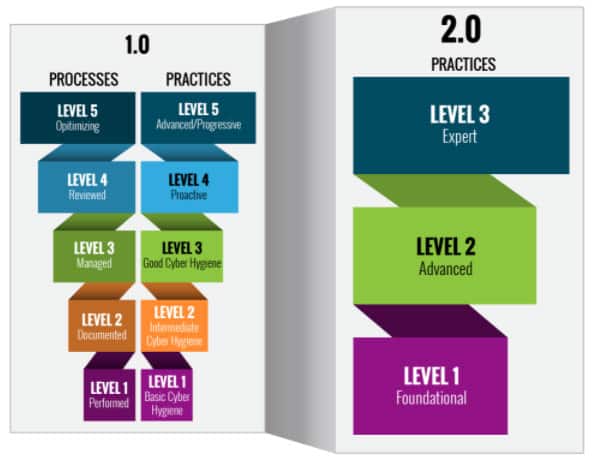

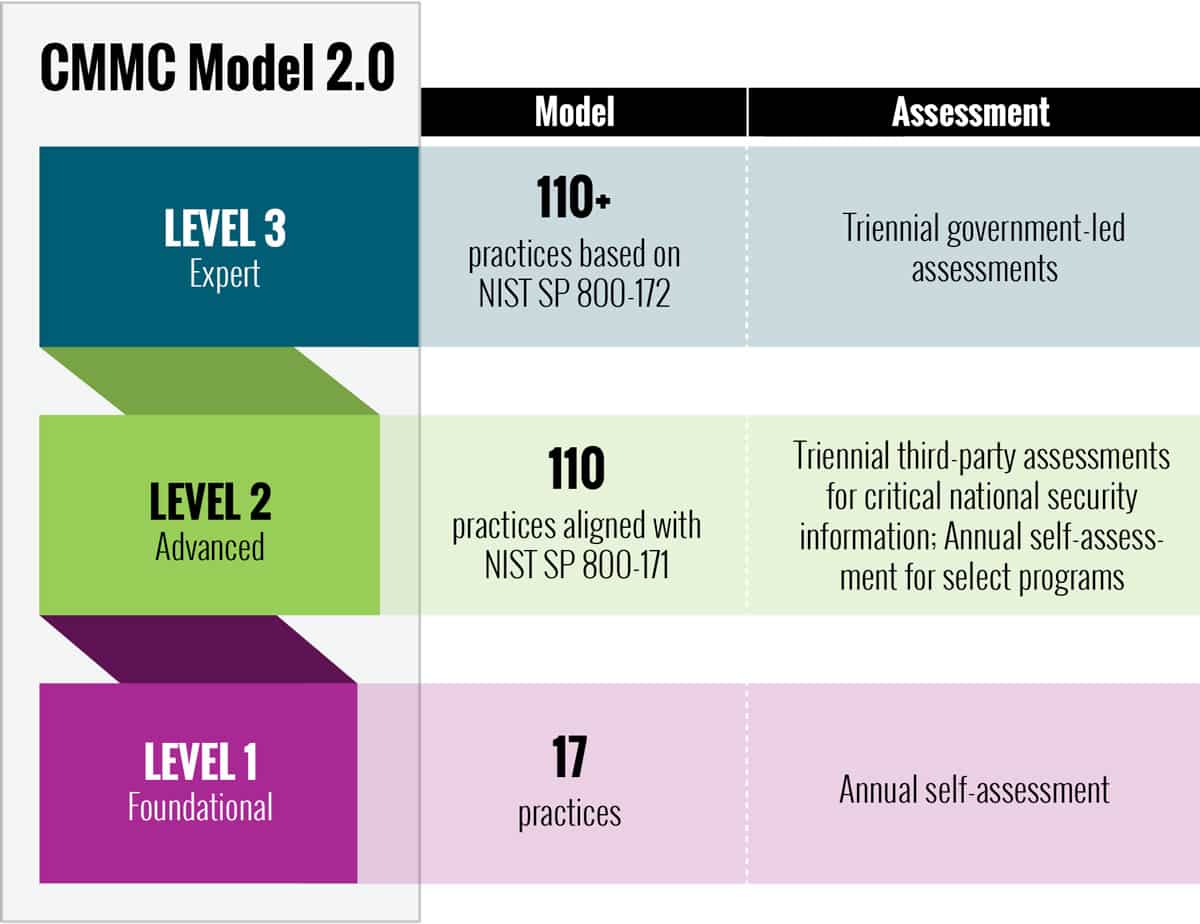
 Typically the first thing you’ll need to do is conduct an assessment of your current IT infrastructure against the control framework that aligns with your desired
Typically the first thing you’ll need to do is conduct an assessment of your current IT infrastructure against the control framework that aligns with your desired 
 The CMMC Accreditation Body (CMMC-AB)
The CMMC Accreditation Body (CMMC-AB) The DoD created CMMC as a “verification component” of the
The DoD created CMMC as a “verification component” of the 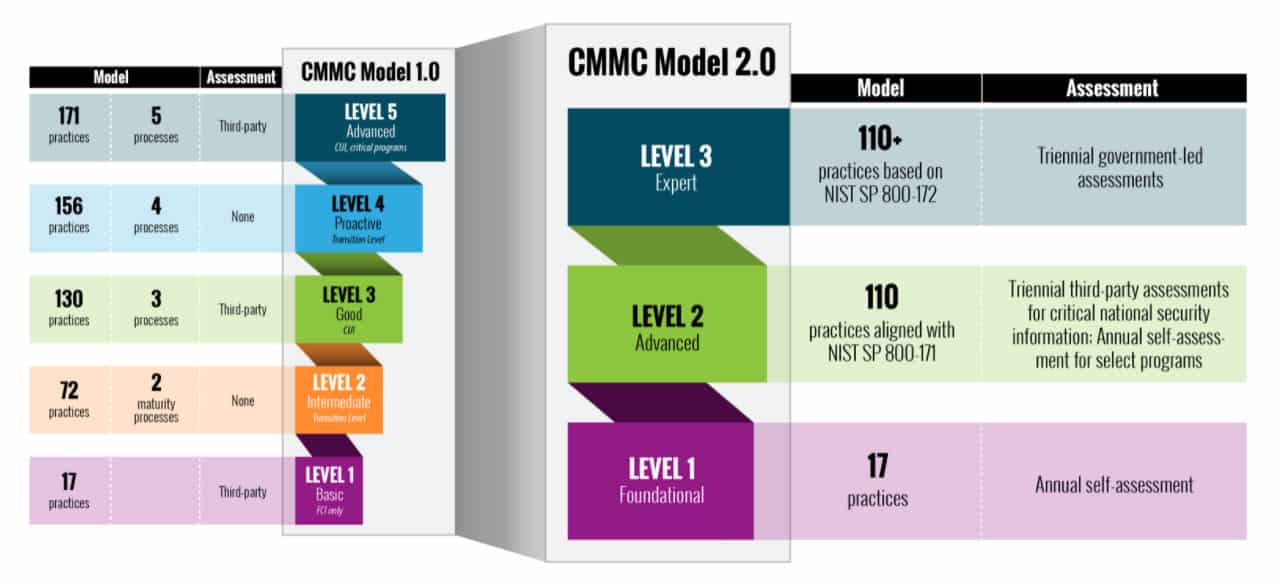
 Commercial businesses and government organizations alike face a growing digital threat from Ransomware, more so now than at any time in recent memory.
Commercial businesses and government organizations alike face a growing digital threat from Ransomware, more so now than at any time in recent memory.